January 11, 2021
River Loop Security’s team members presented at IEEE International Conference on Physical Assurance and Inspection of Electronics (PAINE). The presentation provided a background on hardware implants, secure boot, and background on the Trusted Platform Module (TPM). We then focused on explaining and demonstrating our team’s work developing an TPM interposer and decoder. It concluded in discussing defending agaisnt malicious hardware implants.
Suehayla (Sue) Mohieldin, Cybersecurity and Electrical Engineer at River Loop Security, presented “Decoding & Defending the Trusted Platform Module Against Malicious Hardware Implants” at the virtual conference on December 16, 2020 on behalf of the project team1.
The presentation provided a background on hardware implants, secure boot, and background on the Trusted Platform Module (TPM). We then focused on explaining and demonstrating our team’s work developing an TPM interposer and decoder. It concluded in discussing defending agaisnt malicious hardware implants.
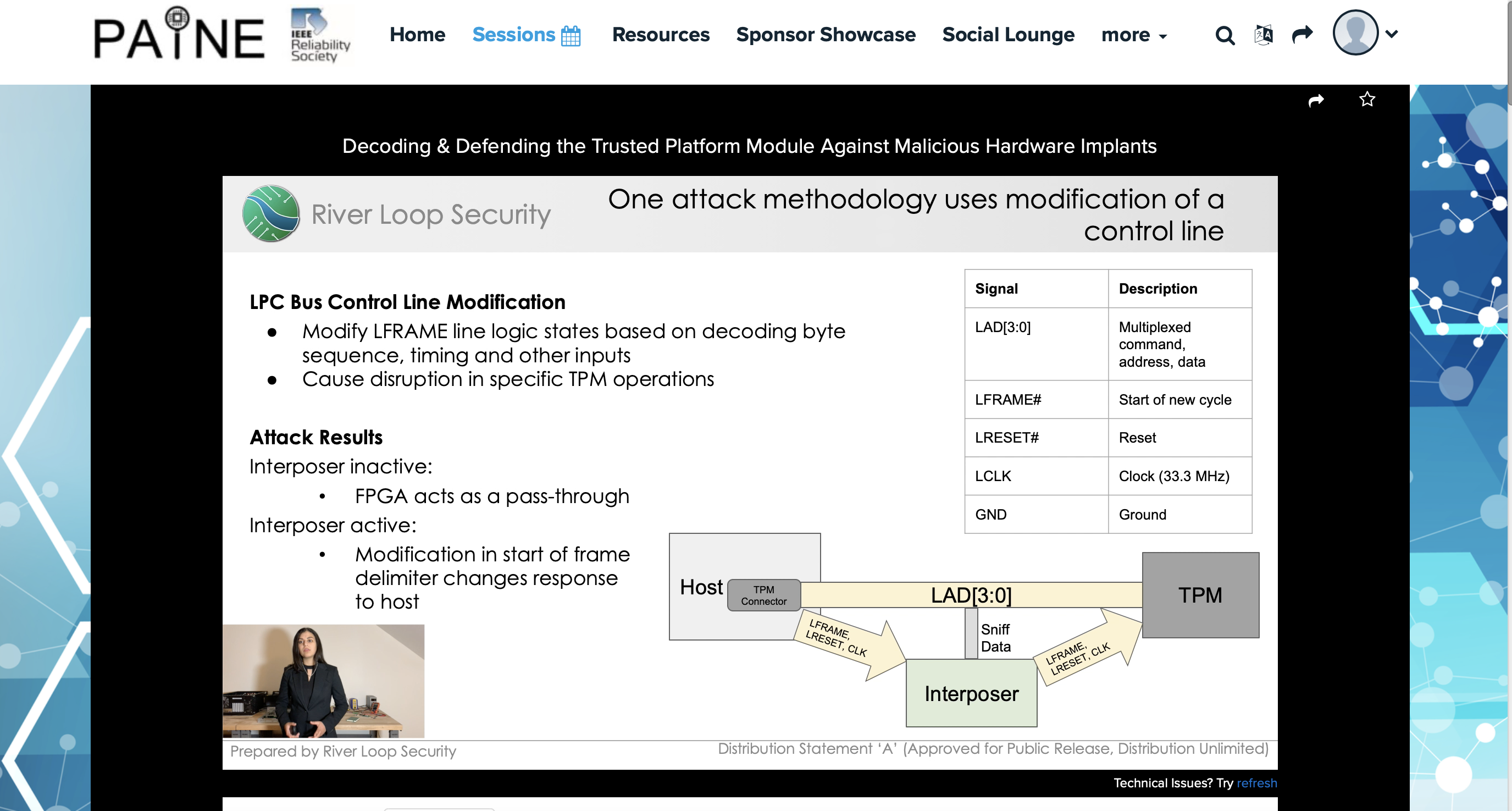
Our TPM interposer presented in this talk was designed to work on a TPM running on a Low Pin Count (LPC) bus, which is a bus commonly used for TPMs in enterprise hardware (e.g., rack mount servers, etc) versus the I2C-bus that prior work on TPM interposers had been conducted on (a I2C TPM for instance is optionally used with a Raspberry Pi).
In addition to developing an interposer which runs in an FPGA, we also created a sniffer that was implemented and tested in Golang, and then was ported to the FPGA to decode traffic and identify signals.
This presentation was based upon work supported by DARPA under the Safeguards against Hidden Effects and Anomalous Trojans in Hardware (or SHEATH)2 program, in the Microsystems Technology Office under DARPA PM Keith Rebello – and we thank them for their support of this research3.
About River Loop Security
River Loop Security is a cybersecurity services firm with deep expertise in IoT, embedded and wireless systems, and supply chain security. River Loop Security provides services including security architecture design, penetration testing, cryptographic protocol design, and security incident response for firms in industries including medical devices, telecommunications, critical systems, and others, with the goal of helping its customers build and deploy more secure products and services which they can stand behind in the market.
We encourage you to contact us if you have any questions or comments based on this announcement.
-
IEEE PAINE Conference. IEEE International Conference on Physical Assurance and Inspection of Electronics. Retrieved December 2020, from http://paine-conference.org/. ↩︎
-
Solicitation No. DARPA-PA-19-04-01 Microsystems Exploration Topic (μE) Safeguards against Hidden Effects and Anomalous Trojans in Hardware (SHEATH). (n.d.). Retrieved October 27, 2020, from https://beta.sam.gov/api/prod/opps/v3/opportunities/resources/files/319e95e6dad1cf0adfb6a2f120b0f40b. ↩︎
-
This material is based upon work supported by the Defense Advanced Research Projects Agency (DARPA) under Contract No. HR0011-20-9-0003. Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the Defense Advanced Research Projects Agency (DARPA). Distribution Statement ‘A’: Approved for Public Release, Distribution Unlimited. ↩︎
